 |
| SHA 256 |
When we have a file that we need to audit against a checksum provided by the file's author, we can use open-source cryptographic software to calculate a checksum. Reviewing the checksum is used for situations where maybe you are at a sketchy website or you don't know if your favorite site is being spoofed.
A hash is not ‘encryption’ – it cannot be decrypted back to the original text (it is a ‘one-way’ cryptographic function, and is a fixed size for any size of source text). This makes it suitable when it is appropriate to compare ‘hashed’ versions of texts, as opposed to decrypting the text to obtain the original version.
Such applications include hash tables, integrity verification, challenge handshake authentication, digital signatures, etc.
SHA-256 is one of the successor hash functions to SHA-1 (collectively referred to as SHA-2), and is one of the strongest hash functions available. SHA-256 is not much more complex to code than SHA-1, and has not yet been compromised in any way. The 256-bit key makes it a good partner-function for AES. It is defined in the NIST (National Institute of Standards and Technology) standard ‘FIPS 180-4’. NIST also provide a number of test vectors to verify correctness of implementation. There is a good description at Wikipedia.
In this JavaScript implementation, I have tried to make the script as clear and concise as possible, and equally as close as possible to the NIST specification, to make the operation of the script readily understandable.
This script is oriented toward hashing text messages rather than binary data. The standard considers hashing byte-stream (or bit-stream) messages only. Text which contains (multi-byte) characters outside ISO 8859-1 (i.e. accented characters outside Latin-1 or non-European character sets – anything with Unicode code-point above U+FF), can’t be encoded 4-per-word, so the script defaults to encoding the text as UTF-8 before hashing it.
In this article, I will demonstrate how to compare the SHA-256 hash of a file downloaded with the one provided by the file's author first on a Windows system, and then on Kali Linux.
Method 2Using UNXZ on Kali Linux
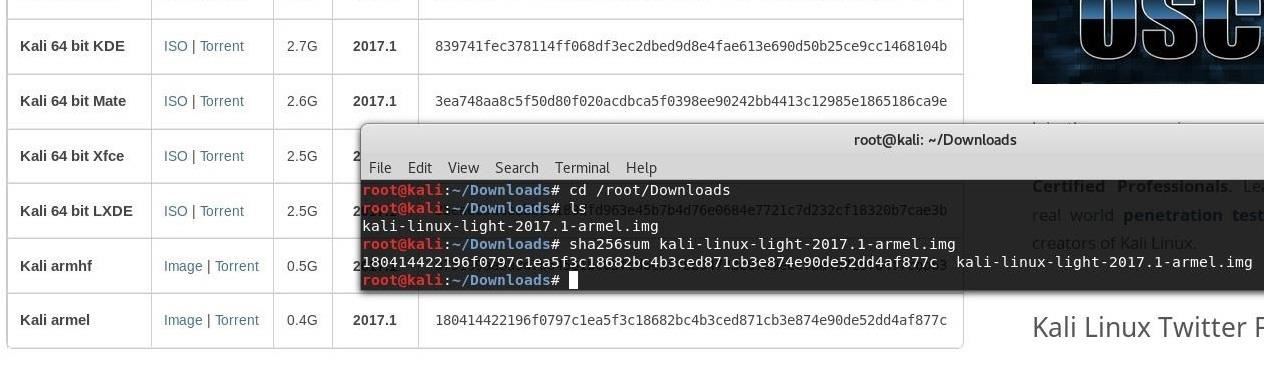
Now let's open our favorite Linux distro, Kali Linux, and open up the browser.Once the image has been downloaded, open up a terminal window and use cd to navigate to the folder where you downloaded the file to. There are many ways to unzip a file on Linux, but what worked for me was a command included by default in Kali called unxz. Run it followed by the path to the file to unzip the ISO image you downloaded.
Once that is extracted, we want to type the following into a terminal window. Make sure "2017.1" is replaced with the current version you downloaded.
sha256sum kali-linux-light-2017.1-armel.imgHit return and the checksum for the file will be displayed in the terminal window. Now, you can compare against the checksum provided by the website. They should match, as shown in the image below.





![The life of an Ethical Hacker [Q&A] | How to become a Hacker](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhd3MEnEzHcekdZnZ6JBlgySIXspWItV8cE9butJaS7Xupfw_h-pVaZPSGhAYDaDq4ANW2M1yOfNTtA9AZ8o52PqYS61s2_HsLNaOkSnXDU7v7_Dzh5ZCKubDqci8IxMSLcPl7CYGcHhpQ/s72-c/hacker+poster.jpg)
Regardless of whether the deals for the business don't build, each deal that occurs through Bitcoin implies less cash is lost because of charges and extortion. bitcoin mixer
ReplyDelete